The VAST data leak
February 27. 2017 0 Comments
- Posted in:
- Security
February 27, 2017
Earlier this month it was brought to my attention that VAST, a prominent WiFi provider in South Africa, had private user information exposed on publicly visible pages on their complimentary internet access portal. The problem was fixed within an hour of being reported to the CTO and went above and beyond by performing a full audit with SensePost to ensure that their customer's data is protected.
All pages on the portal could be accessed through a node number, in a URL format like this: https://portal.vast.directory/node/1234567. As you can see, you are not authorized to see this page any more, but before a fix was applied it looked something like this:
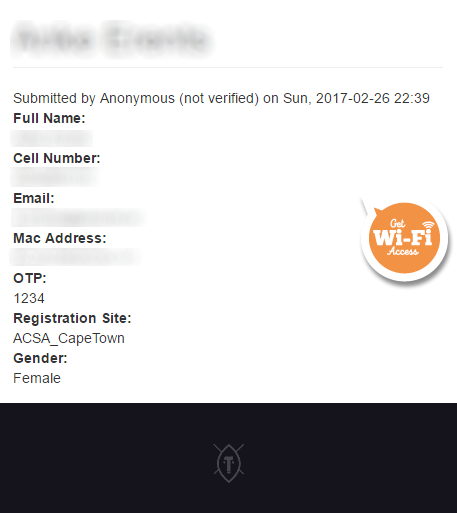
In a nutshell, when you signed up for free/complimentary WiFi on the VAST portal, a new page would be created with the information that you used to sign up. This user provided information included your name, email address, mobile number, verification OTP number (only necessary at certain hotspots), your device MAC address, current hotspot location and gender.
A basic manual enumeration in the browser (adding or subtracting one from the ID portion of the URL) didn't really yield much information so on the surface this did not look significant at all.
At the time this was a gimmick because you could sign on with a fake phone number, get to the page that was generated for you to view the OTP and get free timed access. This escalated when it was realised that you can use the MAC address as both the username and password to create a login session, effectively being able to login as anyone who ever signed up. Using the same MAC address, you could also log anyone off the network, causing quite an annoying denial of service. Many of these exploits were being discussed on security forums and chats as early as the 7th of February. This highlights that there could certainly be some security flaws in the implementation, but I was more interested in the amount of private user information that was accessible.
VAST runs some well known WiFi offerings so I expected to see quite a lot of data. The earliest user account found in the node pages was created in April 2016, so anyone signed up in the last ten months at certain sites could have had their personal information seen by a third party. Of the over 14 million possible node pages, just over 10% actually contained user content, which is still a lot...
In total there are 881,974 unique email addresses and 856,648 unique mobile phone numbers. Some of this information is of course fake, but most people generally don't provide fake data when signing up for these things. Mobile numbers are mostly South African, but there is a fair share of international dialing codes so this would have impacted people who visited South Africa as well and used WiFi at the airport.
If people were using these WiFi hotspots regularly, it was easy to start tracking their movements based on the sites, which flights they were on, where they were travelling, where they often had lunch or restaurants they work from. This was no hack, no technical vulnerability, just a simple page enumeration due to lack of access control to pages containing user information.
I must applaud VAST's response and reaction time to this, one of the fastest I've ever experienced by patching this up in under an hour after being notified. Furthermore, they have engaged with SensePost to review the client implementation and more than likely preventative measures to avoid this in future.
Earlier this month it was brought to my attention that VAST, a prominent WiFi provider in South Africa, had private user information exposed on publicly visible pages on their complimentary internet access portal. The problem was fixed within an hour of being reported to the CTO and went above and beyond by performing a full audit with SensePost to ensure that their customer's data is protected.
All pages on the portal could be accessed through a node number, in a URL format like this: https://portal.vast.directory/node/1234567. As you can see, you are not authorized to see this page any more, but before a fix was applied it looked something like this:

In a nutshell, when you signed up for free/complimentary WiFi on the VAST portal, a new page would be created with the information that you used to sign up. This user provided information included your name, email address, mobile number, verification OTP number (only necessary at certain hotspots), your device MAC address, current hotspot location and gender.
A basic manual enumeration in the browser (adding or subtracting one from the ID portion of the URL) didn't really yield much information so on the surface this did not look significant at all.
At the time this was a gimmick because you could sign on with a fake phone number, get to the page that was generated for you to view the OTP and get free timed access. This escalated when it was realised that you can use the MAC address as both the username and password to create a login session, effectively being able to login as anyone who ever signed up. Using the same MAC address, you could also log anyone off the network, causing quite an annoying denial of service. Many of these exploits were being discussed on security forums and chats as early as the 7th of February. This highlights that there could certainly be some security flaws in the implementation, but I was more interested in the amount of private user information that was accessible.
VAST runs some well known WiFi offerings so I expected to see quite a lot of data. The earliest user account found in the node pages was created in April 2016, so anyone signed up in the last ten months at certain sites could have had their personal information seen by a third party. Of the over 14 million possible node pages, just over 10% actually contained user content, which is still a lot...
In total there are 881,974 unique email addresses and 856,648 unique mobile phone numbers. Some of this information is of course fake, but most people generally don't provide fake data when signing up for these things. Mobile numbers are mostly South African, but there is a fair share of international dialing codes so this would have impacted people who visited South Africa as well and used WiFi at the airport.
If people were using these WiFi hotspots regularly, it was easy to start tracking their movements based on the sites, which flights they were on, where they were travelling, where they often had lunch or restaurants they work from. This was no hack, no technical vulnerability, just a simple page enumeration due to lack of access control to pages containing user information.
I must applaud VAST's response and reaction time to this, one of the fastest I've ever experienced by patching this up in under an hour after being notified. Furthermore, they have engaged with SensePost to review the client implementation and more than likely preventative measures to avoid this in future.
- The page data did not contain any passwords so there is no reason to panic.
- None of this data was indexed on any search engines.
- This data is not available for public download or being sold anywhere that I know of.
- There is little reason to believe anyone's details were in fact compromised while the exposed pages were visible.
- No, I will not tell you if you are/were in the data, use Troy Hunt's "Have I Been Pwned" service.
